Using bearer token to call recurring integration of D365FnO using logic apps
This article talks about using bearer token to authenticate recurring integration URIs to talk to D365FnO. For our example, we are using an XML based input, which we need to feed into D365FnO (for example: you can think of a feeding an XML to a composite entity). Assuming that we already have an enqueuing URL in place, we can go to logic apps designer to declare a variable called 'token' for our ease of calculations:
We can call the token generating URL, through a HTTP POST request connecter in our Logic apps, as follows:
Here the URI implies: the token generator URI, from "https://login.microsoftonline.com"
Header: set 'Content-type' as 'application/x-www-form-urlencoded'
In Queries set: 'Grant_Type' = 'client_credentials'
And in the body, set Client_Id = <Client Id from your App registration>, add your client_Secret by appending '&'. Client_Secret = <from your app registration>, add grant_type= 'Client_credentials' by appending a '&' and finally append scope which is = <base URL of D365FnO>
Alternately: you can save these parameters in an Azure Key Vault, and then fetch them here to avoid writing these variables as open literals.
Typically the output looks like this:
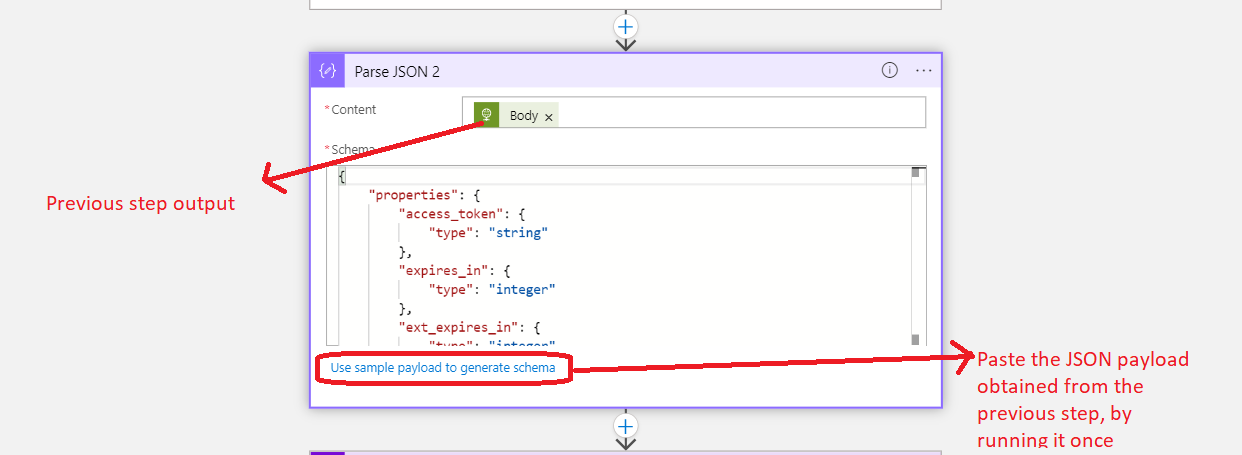
You need to get the value of 'Access_token' from the above JSON. This could be done by parsing the Json like this:
You can now set the value of the bearer token in the 'token' variable which you have declared above:
In the Header, you need yo pass on: 'Authorization' value as 'Bearer <token variable value obtained from above>' (Don't forget to include a space between 'Bearer' and the token value). In the body, you need to send the XML content which you receive as an input. This will do the needful of insert/update, based on the recurrence time, which you have set for your batch execution.
Additionally you can keep the last step inside a loop, so as to wait till the execution gets completed or throw error on failure.








Comments
Post a Comment